“username or password incorrect” is bullshit
There’s a security best practice where sign ins aren’t supposed to say “password is incorrect”. Instead they’re supposed to say the “username or password is incorrect”. This “best practice” is bullshit.
Stripe and GitHub’s sign ins for example follow this practice.

The idea is if an attacker knows a username, he or she could concentrate on that account using SQL injection, brute forcing the password, phishing, and so on.
Here’s the problem.

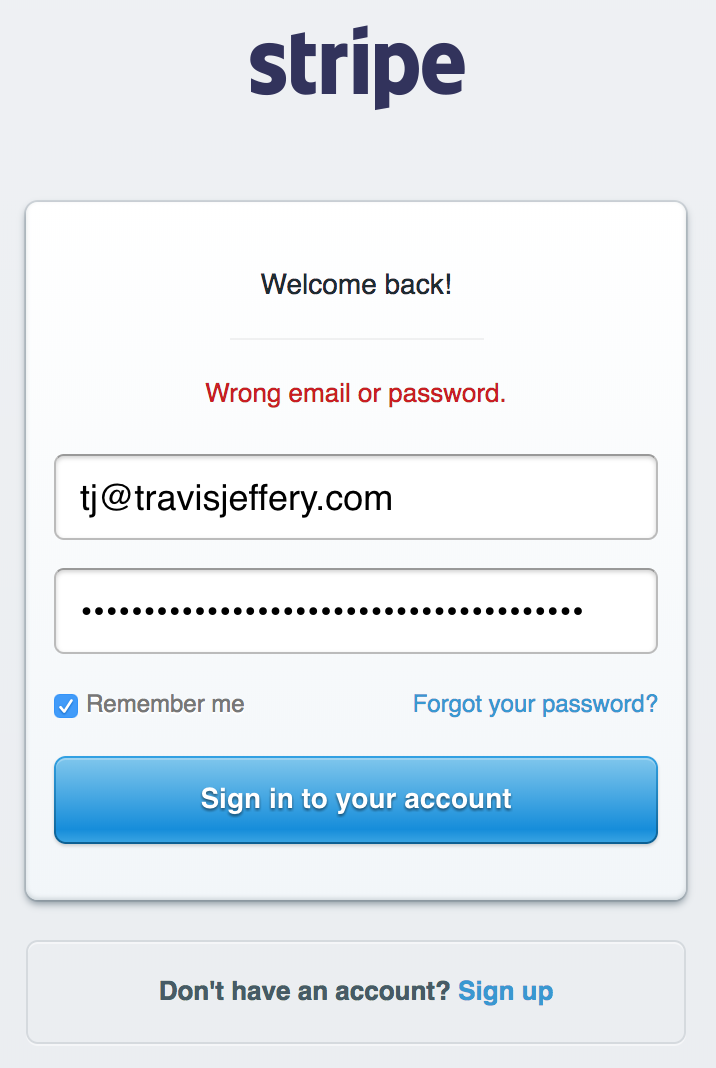
Stripe’s sign up page.
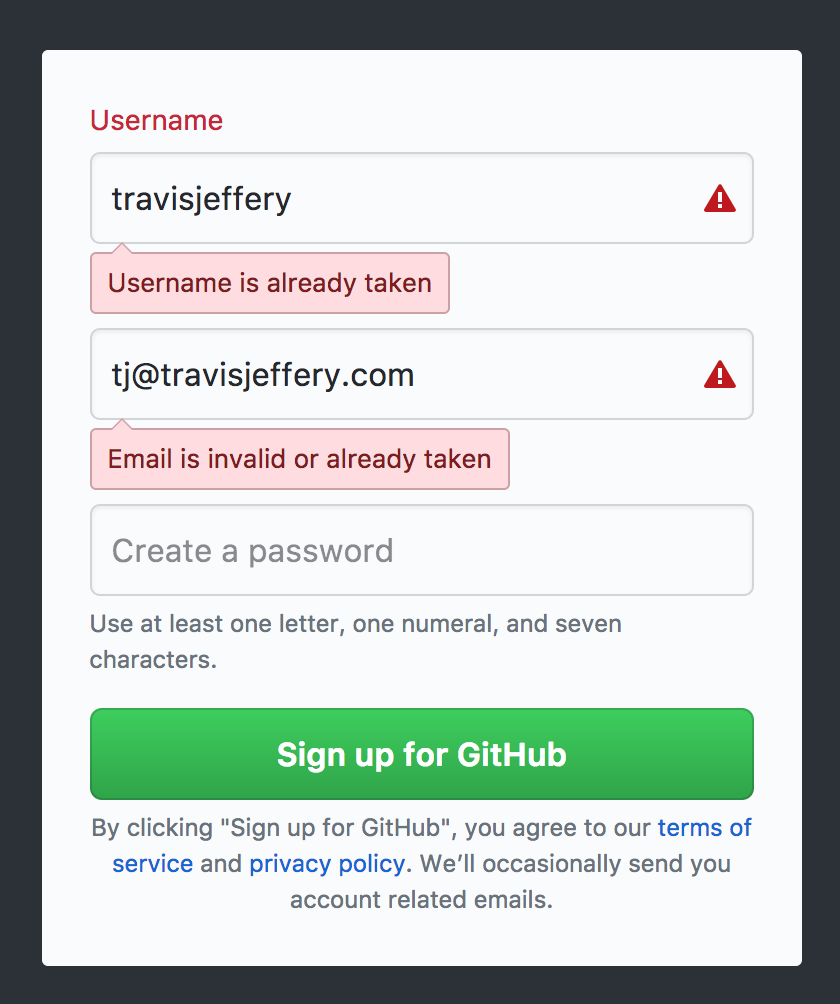
Shit, y’all know my username… Guess I’m fucked. Not to mention you could’ve just gone to https://github.com/travisjeffery.
All a hacker has to do is sign up to know whether the username is valid or not. Why bother then with obfuscating the sign in? Only the dumbest, laziest hacker is stopped by the “username or password is incorrect” sign in. You gain no security, yet your customers lose clarity.
Stripe has their form submission behind reCAPTCHA to prevent naive scripts attacking their sign up. However this has been broken multiple times (1, 2) and likely won’t ever be perfect. Even if reCAPTCHA was perfect, a hacker could manually validate their usernames of interest by trying to sign up, then automate an attack on the sign in page.
To prevent attackers from knowing whether an account exists or not your signup must only take an email address and provide no feedback in the UI if the sign up succeeded or not. Instead the user would receive an email saying they’re signed up. The only way an attacker would know if an account exists is if they had access to the target’s email.
Barring that, “username or password incorrect” is just bullshit.
–
Please say hi at @travisjeffery.
Hit the 👏 and share if you found this useful.
Thanks for reading.
